- Date:
- 2016-2018
- Themes:
- Crowd Sourcing, Social Machinery
- Funding:
- European Commission (H2020 CAPS)
WHY: 2015 has been named by the United Nations as the International Year of Light (light2015.org). Light has had many obvious benefits for human mankind, but it also poses some relevant threats: the everyday-increasing excess of light thrown by humans to the sky seriously threatens to remove forever one of humanityââ¬â¢s natural wonders, the view of our universe. More importantly, it has also an adverse impact on our environment and economy (energy wasted to the sky costs 2 billion US$ per year in the USA and 6,3 billion â⬠per year in Europe) and on the health of hundreds of species, including pathologies in human beings (e.g., stress, insomnia). Many professional and amateur scientists are already fighting against light pollution. However, it is necessary to increase social awareness about the importance of preserving the darkness of our cities and environment.
WHAT: STARS4ALL will create an Light Pollution Initiative (LPI) incubation platform that will allow generating (and maintaining) customizable on-demand domain-focused LPIs (e.g., a light pollution working group in Brussels). The platform will be self-sustainable: it will integrate a crowdfunding tool to obtain funding for the LPIs; it will consider incentives that motivate citizens to participate in LPIs, as well as policies to handle those incentives; and it will provide innovations in data acquisition from sensors deployed by citizens and in games with a purpose.
HOW: STARS4ALL will initially deploy 10 LPIs, which will be available by the end of the 1st semester of project execution, and will be operating and creating collective awareness during the rest of the project. At that moment we pave the way the creation of other LPIs by citizens, specially in other disciplines such as Energy Saving, Biodiversity, and Human Health, and will organize open competitions among them.
Primary investigator
Secondary investigators
- ntr1g09
- ic1f17
Partners
- UNIVERSIDAD POLITECNICA DE MADRID
- CEFRIEL - SOCIETA CONSORTILE A RESPONSABILITA LIMITATA
- EUROPEAN CROWDFUNFIND NETWORK
Associated research group
- Web and Internet Science
- Date:
- 2015-2017
- Themes:
- Open Government Data, Open & Linked Data, Web of Data
- Funding:
- H2020 (644683)
The Open Data Incubator for Europe (ODINE) is a 6-month incubator for open data entrepreneurs across Europe. The programme is funded with a ââ¬7.8m grant from the EUââ¬â¢s Horizon 2020 programme and is delivered by the seven partners featured below.
ODINE aims to support the next generation of digital businesses and support them to fast-track the development of their products. We are already championing the best of European digital talent and look forward to more outstanding companies to incubate.
Primary investigator
Secondary investigator
Partners
- Open Data Institute
- Fraunhofer IAIS
- Telefonica Open Future
Associated research group
- Web and Internet Science
Masters of Science graduates
MSc graduates from India, Cyprus, Mexico, Greece and the UK share their experiences as an Electronics and Computer Science student at the University of Southampton

Video Tutorial
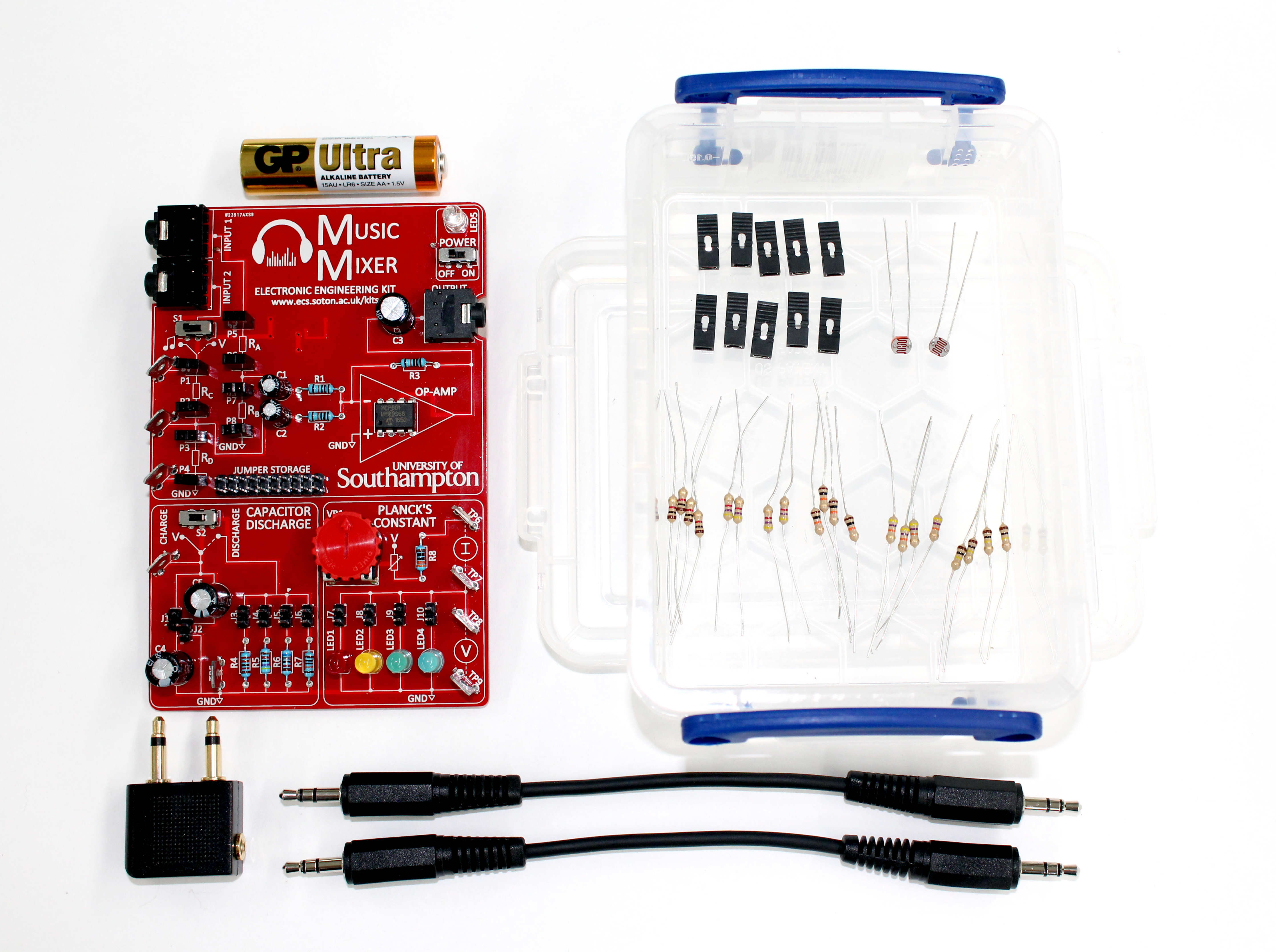
This tutorial video walks viewers through the typical use of the Planck’s Constant part of the kit, and the experiment described in the accompanying exercise notes.
Video Tutorial
This tutorial video walks viewers through the typical use of the Capacitor Discharge Section part of the kit, and the experiment described in the accompanying exercise notes.
Video Tutorial
This tutorial video walks viewers through the typical use of the Music Mixer and the experiment described in the accompanying exercise notes.
Operational Amplifiers
This video explores the functionality of an operational amplifier, how it is used in the Music Mixer kit, and some of the other uses of this widely used electronic component.
Potential Dividers
This video explores the potential dividers on the Music Mixer kit, how they are used to mix the two input channels, and the wider applications of this technology.